
Overview
In today’s world, the internet has become the backbone of almost every business operation. From communication to data sharing, the internet has transformed how we work, but it has also brought significant cybersecurity challenges. As organizations continue moving their business-critical applications and data to the cloud, the need for secure and reliable connectivity has never been more critical.
To address these challenges, leading government cybersecurity organizations have come together to introduce the Trusted Internet Connections (TIC) initiative, which defines a set of security guidelines to ensure secure connectivity between government networks and the internet. The TIC program has evolved over the years. The latest version, TIC 3.0, is designed to support cloud adoption and provide a more secure and flexible internet connection to federal agencies.
In previous TIC versions, the agency traffic needed to flow through a physical TIC access point, which has proven to be an obstacle to adopting cloud-based infrastructure. For example, TIC 2.0 focused exclusively on perimeter security by channeling all incoming and outgoing agency data through a TIC access point.
Alkira, a leading provider of the multi-cloud network as a service (NaaS) solutions, has taken a proactive approach to address the security challenges of cloud connectivity. Alkira’s Cloud NaaS platform is built to meet TIC 3.0 guidelines and provides a secure and scalable way to connect to multiple clouds.
This blog will explore how Alkira’s Cloud NaaS platform can help federal agencies meet TIC 3.0 requirements and provide secure cloud connectivity.
Native Cloud Networking Design and Challenges for TIC 3.0
Federal customers who are deploying workloads in the cloud need to make sure that requirements around TIC 3.0 are taken into consideration
- Zero Trust Policy for traffic inbound and outbound from the internet
- Allow traffic from known devices
- Ability to manage user activities using audit logs and their access to specific functions and information
- Ability to isolate departments within an organization and configure specific security policies for each department
- Visibility into flows and security rules
- Encryption for all traffic to make sure data integrity is maintained
- Any traffic threats should be detectable immediately using alerts and notifications
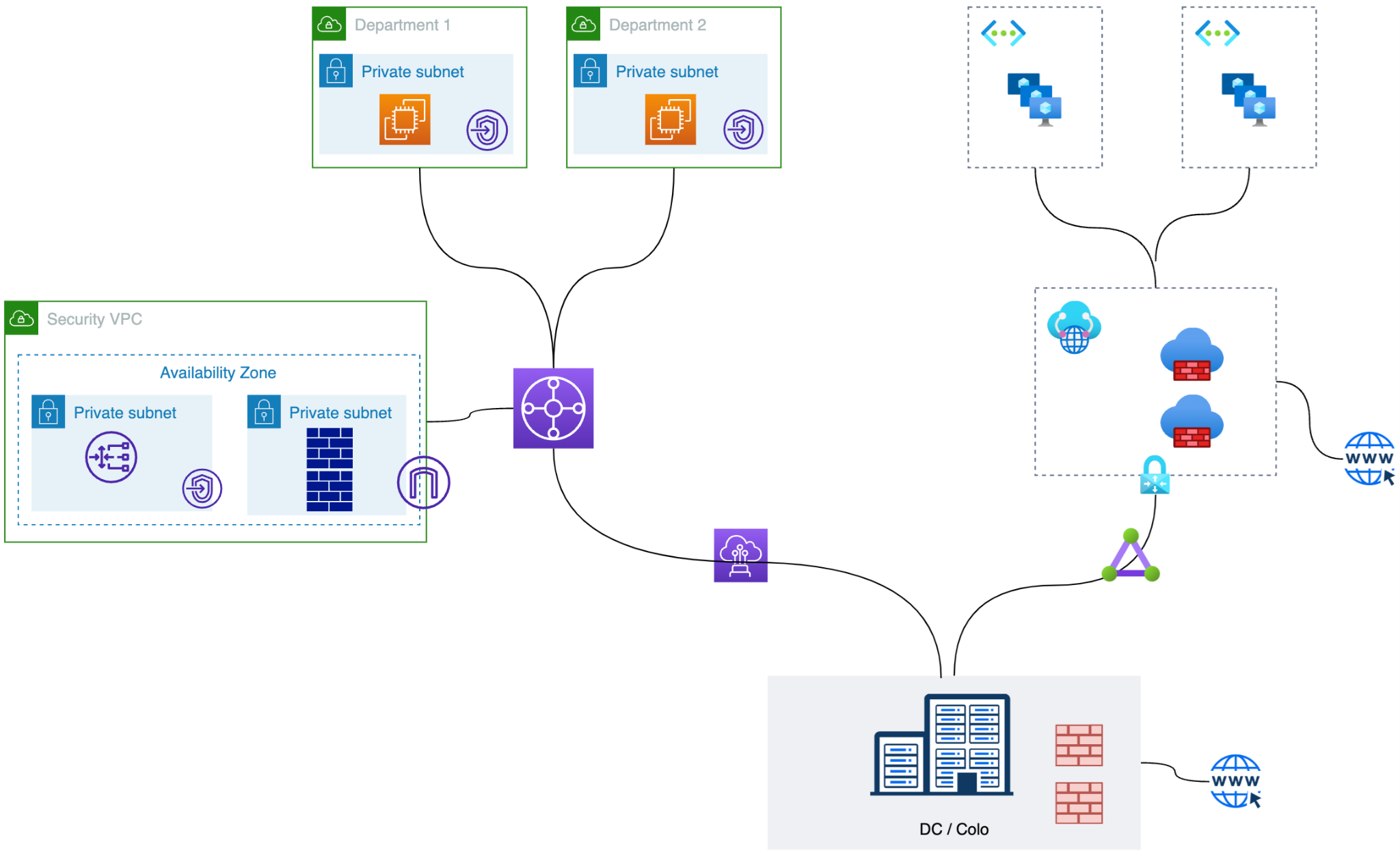
Figure 1: Trusted Internet Connections (TIC) 3.0 Native Approach
Native constructs of major CSPs fail to fulfill the above requirements. Here are some challenges using native constructs in CSPs:
- Segmentation is impossible using the Cloud Native approach, which is essential for Government customers that need insulation between workloads or resources between different business units or departments. If workloads are deployed across multiple clouds, this becomes a bigger challenge.
- Encryption is an important requirement for Government customers, but using cloud-native functionality might only be possible for some traffic. For example, private connectivity options using Cloud native constructs do not provide encryption; any encryption would come at the cost of performance.
- Visibility into real-time traffic flows is limited using cloud-native functionality, meaning troubleshooting any network issues would be challenging in these environments.
Alkira Cloud Networking-as-a-Service for Trusted Internet Connections (TIC) 3.0
Alkira Cloud NaaS is the first global unified multi-cloud network delivered as-a-service. Alkira seamlessly solves the requirements for TIC 3.0 and the challenges mentioned above. Alkira allows customers to quickly onboard their on-premise infrastructure by leveraging various methods, including AWS Direct Connect, Azure Express Routes, Remote VPN/ZTNA clients, and IPsec/SD-WAN Connections from their DCs, or government offices into the Alkira Cloud Exchange Points. At the same time, customers connect their cloud workloads (VPCs, VNETs, VCNs etc.) to the Alkira Cloud Exchange Points. Alkira’s solution also allows customers to inspect the traffic between on-premise to cloud or multi-cloud environments to use a policy-driven framework to steer traffic to their desired security solutions as per the requirements. In addition, visibility into all traffic flows is available for any endpoints connected to the Alkira CXP.
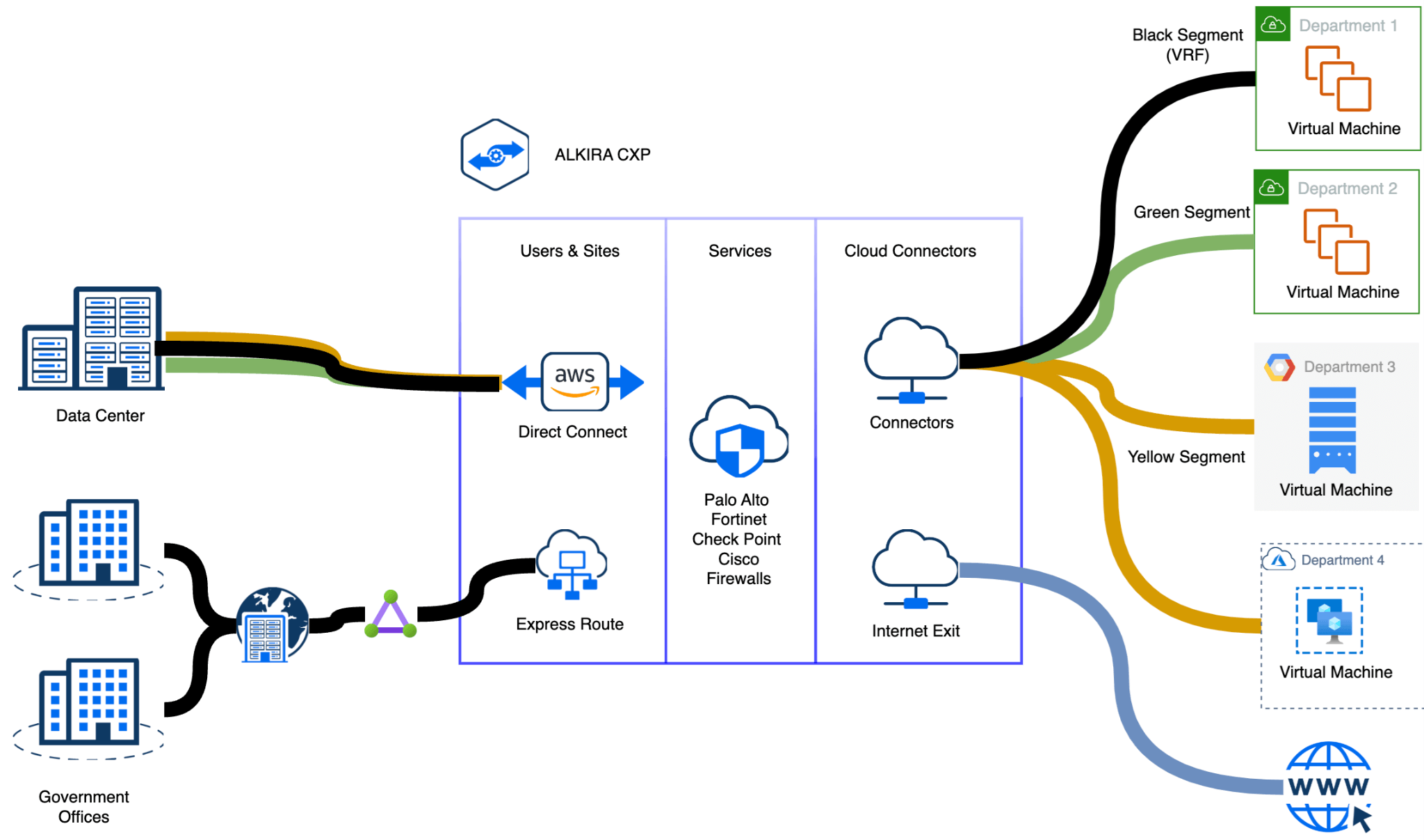
Figure 2: Alkira Trusted Internet Connections (TIC) 3.0 Approach
Federal agencies can leverage any major CSPs from Azure, GCP, AWS, and OCI. The above architecture provides an optimal and secure path for Internet Ingress-Egress traffic across a multi-cloud environment; there is no need to backhaul internet traffic to on-prem for firewall inspection.
Alkira Platform Benefits
High Availability and Resiliency
Alkira’s infrastructure is built in the cloud, for the cloud. The Alkira Platform is highly resilient to leverage the full scale and flexibility of the major CSP’s. All aspects of our architecture are redundant and spread across discrete availability zones (AZ’s) and available across multiple regions to allow our customers to achieve their critical SLA requirements.
Segmentation and Micro-Segmentation
Alkira segments are completely isolated route domains or VRFs. Hence for third-party clients complete isolation of workloads can be achieved using these segments. Traffic across segments can be inspected as well. Since a segment represents a unique routing and policy space, maintaining isolation becomes seamless for customers. Based on customer requirements these segments can also be extended across multiple regions if workloads are deployed in those regions.
Refer to this blog for more details about cloud network segmentation.
Seamless Firewall Integration
Alkira’s platform is highly integrated and tightly automated with vendors like Check Point, Cisco, Fortinet, Palo Alto, and ZScalar for traffic inspection for any type of traffic flow. Federal organizations get a significant advantage as they don’t have to bring up firewalls depending on traffic flow. Also, functionality like autoscaling comes as part of the solution, which helps to scale up or down depending on the requirements.
For more details, please refer to this multi-cloud inline traffic inspection blog.
Visibility
Alkira Cloud Insights helps discover all cloud resources along with their networking & security configurations, Detect threats and security vulnerabilities, Optimize and reduce your cloud spending by deleting unused resources, repurposing idle infrastructure, and maximizing efficiency across Multi-Cloud deployments. Last but not least, Alkira Cloud Insights can help Federal organizations improve the speed and responsiveness of cloud applications by fixing complex network misconfigurations.
Encryption
Alkira Cloud Network-as-a-Service platform ensures end-to-end encryption for the traffic flows within the infrastructure and gives customers control to onboard their workloads using IPSec.
Latency
Customers can connect to the Alkira Platform in the nearest region, wherever their users and workloads exist, and from their local Cloud Exchange Point (CXP), leverage the Alkira Backbone to have low latency while connecting to these applications. This can help with applications that are latency-sensitive and assist with efficient connectivity.
Automation with Terraform
Large-scale network infrastructure deployments require automation, and Alkira helps solve this, wherein the customer can use Terraform to provision the network infrastructure for Alkira.
Conclusion
The TIC 3.0 guidelines provide a framework for federal agencies to ensure secure internet connectivity. Alkira Multi-Cloud Network-as-a-Service Solution is built to meet these guidelines and provides a secure and scalable way to connect to multiple clouds. The Alkira Cloud NaaS solution provides a cloud-native architecture built on global network infrastructure, providing a comprehensive set of network services such as security, routing, load balancing, and optimization.
Alkira’s comprehensive security features, such as end-to-end segmentation, encryption, and threat detection, help protect against cyber threats and ensure the network infrastructure is secure. This solution also provides a flexible and scalable network infrastructure that can adapt to changing business needs.
Overall, Alkira is a reliable and secure platform that meets TIC 3.0 guidelines and provides a seamless way for federal agencies to connect to multiple clouds. A secure and reliable network infrastructure is crucial as organizations continue to move their critical workloads to the cloud. Alkira’s Cloud NaaS solution provides a modern approach to the network infrastructure that helps organizations manage their network infrastructure easily and securely.
Schedule a demo today to see how Alkira can help accelerate your TIC 3.0 initiatives.

Ahmed Abeer is a Sr. Product Manager at Alkira, where he is responsible for building a best-in-class Multi-Cloud Networking and Security Product. He has been in Product Management for more than ten years in different big and small organizations. He has worked with large enterprise and service provider customers to enable LTE/5G MPLS network infrastructure, automate Layer 3 Data Center, enable Next-Gen Multi-Cloud architecture, and define customers’ Multi-Cloud strategies. Ahmed’s technical expertise in Cloud Computing and Layer 2/Layer 3 network technologies. Ahmed is a public speaker at various conferences & forums and holds a Master’s Degree in Computer Engineering

Deepesh Kumar is a Solutions Architect and product specialist in the computer networking industry with over 8 years of experience. He currently works as part of the post sales team at Alkira and focuses on working with customers to design and deploy the Alkira solution. Prior to working here, he worked at Viptela which was acquired by Cisco Systems. He holds a masters degree from San Jose State University.



