
The last few years have seen modern day enterprise networks being massively disrupted. On one hand, applications and data are migrating from on-premises locations to the cloud. On the other hand, most users who previously accessed these applications and data from predetermined on-premises locations, are now accessing them from diverse locations working from home or just being mobile. Both these disruptions combined have led to significant connectivity demand and put a major strain on traditional remote access solutions. Alongside connectivity, security plays an ever-significant role. Traditional trust-but-verify models are struggling to keep up with sophistical security attacks, making way for zero trust network access (ZTNA) approach.
The global pandemic has certainly highlighted and exacerbated the above-mentioned disruptions. Many organizations have embraced working remotely as the new normal going forward. There are a few important lessons to be learnt as organizations adapt to the rapidly evolving modern workforce and enterprise applications.
Design Globally
Traditional remote access VPN solutions were deployed by enterprises in on-premises data centers or other centralized locations. It seemed an ideal choice to place the VPN solution in the data center, since that’s where most applications resided. Moreover, the Internet exit points for remote users were oftentimes subjected to a security stack residing in the data center as well. However, with time, many internal applications have migrated from the on-premises data centers to the public cloud and SaaS environments. This has resulted in significant network latency increase and an ever-growing bandwidth demand on the connectivity from the data center to the cloud. Also, working remotely implies that the remote users could practically reside anywhere in the world. As such, having VPN termination, aka VPN concentrators, in the on-premises data center or at specific centralized locations, creates unnecessary traffic backhaul, which further amplifies the latency concerns.
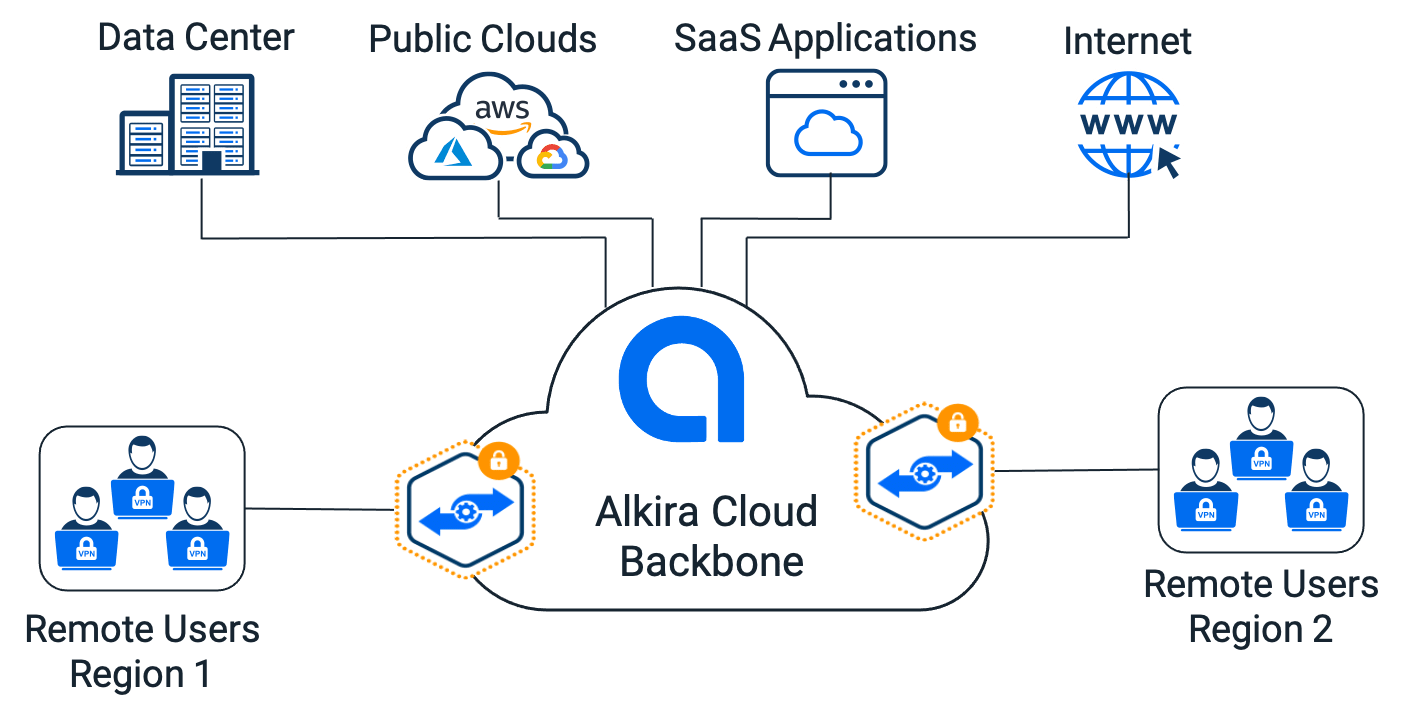
Alkira’s solution accounts for the enterprise applications being distributed across the on-premises data centers, single or multiple public clouds and SaaS offerings. The solution also accounts for the geographically distributed and possibly dynamic nature of the location which remote users are connecting from. As such, it is globally available, distributed and has an ability to dynamically redirect users to the closest network access location (Alkira Cloud Exchange Point) optimized for geography and the destination application.
Design for Scale
Many traditional remote access VPN solutions were designed for only limited or transient use. Oftentimes the expectation was for a small number of concurrent connections to a limited set of applications for a relatively short duration of time. Traditional solutions were not designed with large or variable scale in mind. Doing so would require procuring and installing surplus VPN capacity. To meet the peak demand for concurrent connectivity and throughput, enterprises are now forced to over-provision VPN termination capacity resulting in wasteful infrastructure and licensing costs. Alternatively, enterprises end up under-provisioning VPN capacity to keep the expenses under control, while taking the penalty of lower performance.
Alkira’s solution is both deployable in minutes and is truly elastic at the same time. Enterprises can scale dynamically as the demand for capacity goes up and down over time, preventing wasteful overprovisioning. Akira’s cost model is rooted in a real-time consumption, rather than fixed capital expenditure model based on user-licenses and/or throughput.
Design for Security
It goes without saying that any modern-day remote access solution needs to rise to the security challenges faced by the enterprises. Traditional remote access solutions are based on the age-old “trust, but verify” approach, where, once authenticated, users are granted full access to the network. However, this model is severely lacking when faced with the modern sophisticated threats seen by enterprises today. An authenticated, but compromised remote user, can potentially laterally move across the enterprise network encountering no further security inspections.
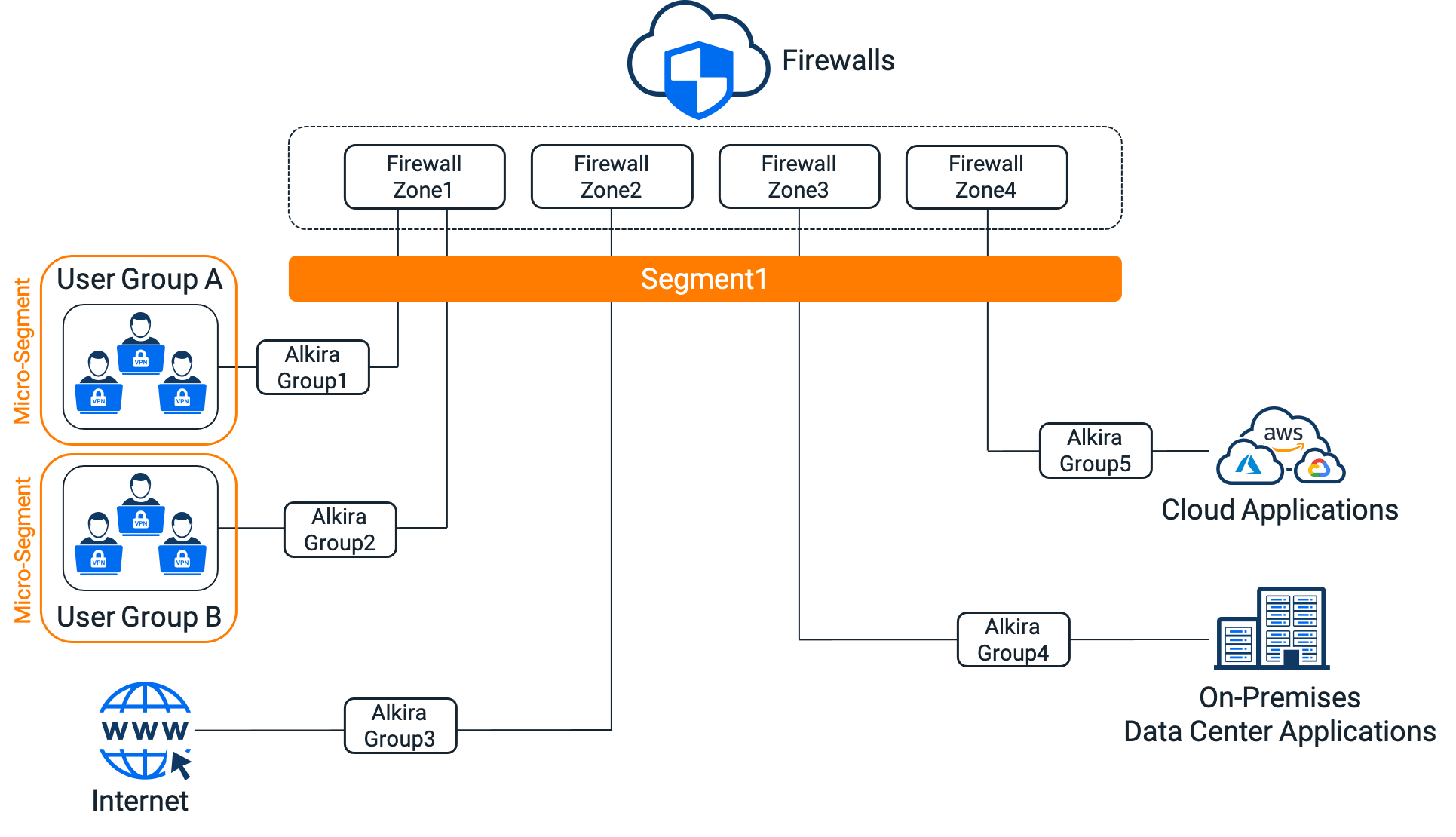
Alkira’s solution is based on a robust zero trust network model where authenticated users are constrained to specific network segments preventing lateral moves across the environment and reducing the overall attack surface. In case of need, remote users’ traffic within a segment [micro-segment] or between segments [shared application services] can be steered to the next-generation firewalls provisioned in the Alkira Cloud Exchange Points for stateful security policy enforcement.
In conclusion, Alkira’s solution addresses the challenges around providing a global, elastic, zero trust network access without compromising end-user experience while accessing on-premises, cloud, multi-cloud, and SaaS applications.
Learn more
- Read solution whitepaper at Elastic ZTNA
- Read multi-cloud networking whitepaper by Atif Khan, Founder and CTO of Alkira https://www.alkira.com/discover
- Request your own personalized demo at https://www.alkira.com/demo



