
In the previous blog, we talked about the Ingress Inspection using Alkira. This blog will focus on Multi-Cloud Inline traffic inspection, which helps you monitor your traffic from malicious actors. Alkira firewall service allows or denies network traffic for real-time flows from source to destination using traffic policies.
We will be covering the following three use-cases:
1- Inspecting traffic between VPC/VNets (East-West Traffic)
2- Inspecting Traffic between Cloud and OnPrem (North-South Traffic)
3- Inspecting the outbound internet traffic from the cloud (Egress Traffic)
CSP Native Approach:
Each use case will be handled differently in the native Cloud Service Provider (CSP) approach. Let’s go over each use case one by one:
Case 1: Inspecting traffic between VPC/VNets (East-West Traffic)
In the Traditional Cloud Service Provider (CSP) approach for East-West traffic inspection, a third-party firewall will be placed in a separate VPC/VNET called a Security VPC/VNET. The traffic will come from the source workload VPC to the destination workload VPC traversing the specific networking constructs (TGW, vWAN Hub, etc.) and then hit the Security VPC where we have 3rd party firewall (e.g., Palo Alto VM-Series, Fortinet FortiGate, Check Point Security Gateway, etc.) for traffic inspection before it reaches to the destination.
As you can see below in the example, many steps are required to solve this use case.
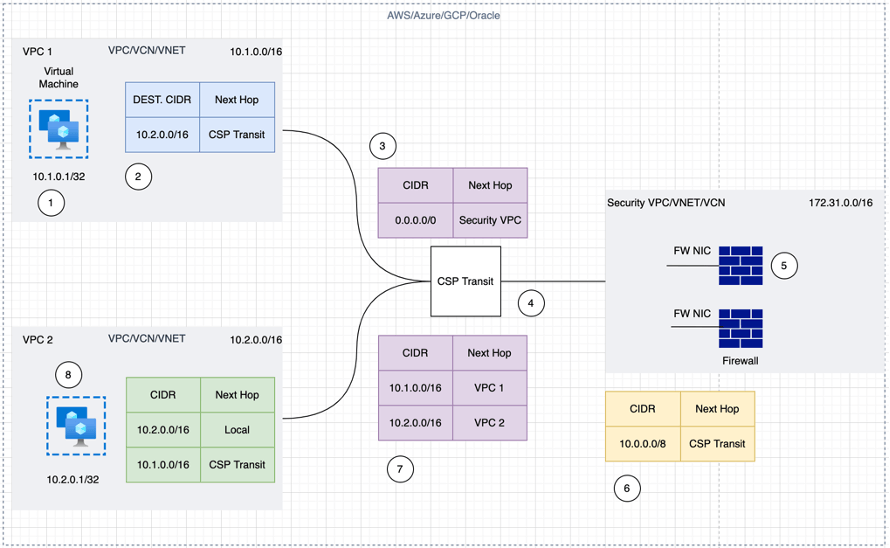
Figure 1: Inspecting traffic between VPC/VNets (East-West Traffic)
Case 2: Inspecting traffic between Cloud and OnPrem (North-South Traffic)
This case is similar to the above use case; Spoke VPC/VNET traffic is going towards On-Prem via a third-party firewall, and similar complexity exists in this use case.
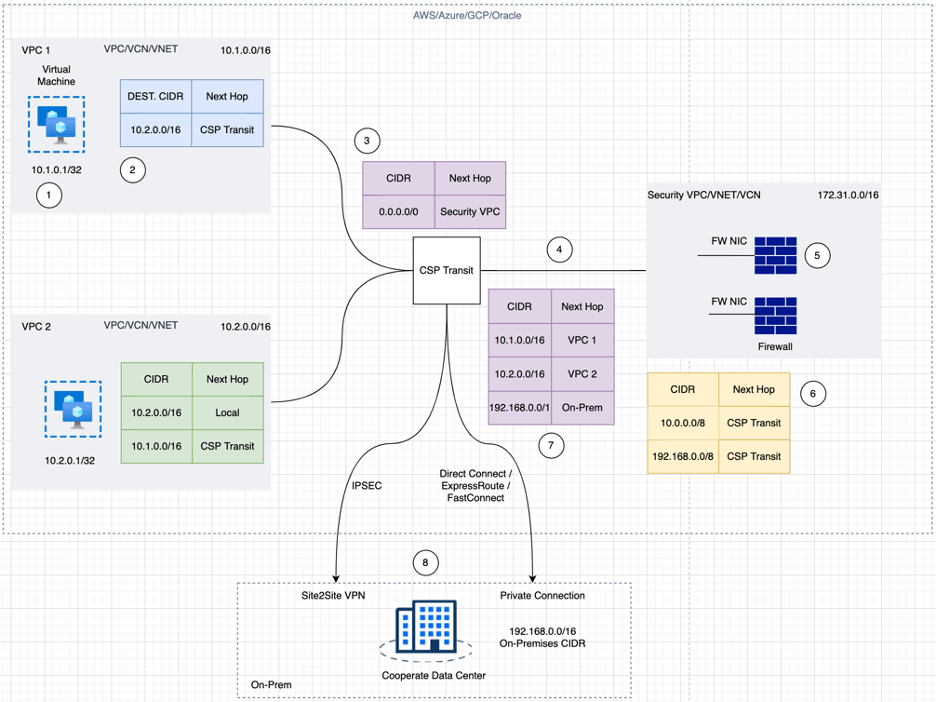
Figure 2: CSP Native Approach for Cloud to OnPrem Inspection
Case 3: Inspecting the Cloud outbound internet traffic (Egress Traffic)
Similar to the prior instances, the traffic will originate from the workload VPC towards the internet via the CSP Transit, as shown in the below example, and then hit the security VPC to go towards the internet. The difference here is that the Source IP of the outbound traffic towards the internet will get translated (SNAT) on the firewall.
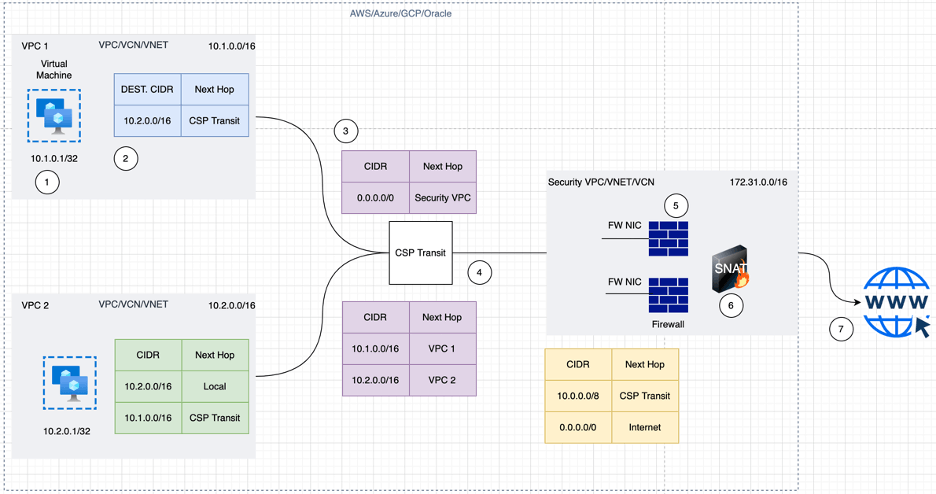
Figure 3: CSP Native Egress Inspection
Problem with this Approach:
Design Challenges at Scale
The design will look different for the above three use cases when a large-scale deployment is done. Taking the case of a single cloud but with multiple regions, setting up the security VPC for traffic inspection would be required. The challenges are even more significant if the same design is used in a multi-cloud environment.
Visibility
Visibility into traffic is a challenge in any CSP environment, which creates a problem in troubleshooting any connectivity issues. Also, since there are multiple networking constructs in each CSP, figuring out where the issue lies is a challenge.
Configuration
Different CSPs have different networking constructs in a multi-cloud environment, which means that configuring each will be complex, and managing these resources will be a pain. Also, each CSP has its own set of limitations for these resources, which creates a design problem for solving these use cases.
Alkira Approach:
Using the Alkira solution, users can handle the above use cases seamlessly once the relevant configuration has been applied to the Alkira CXP.
For each of the above use cases, traffic is redirected to the FW when the policy is applied; once the traffic is inspected, it will be sent to the destination. The firewall policy on Alkira CXP gives flexibility to the user to steer the traffic depending on the use case.
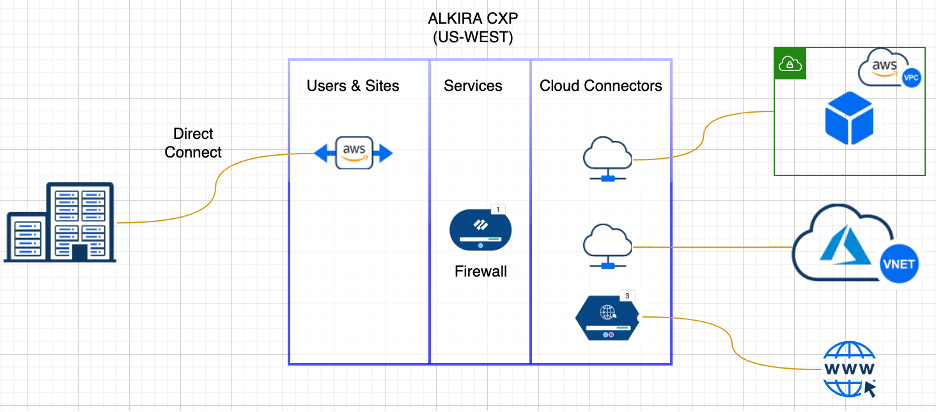
Figure 4: Alkira CXPs make managing and steering traffic simple and easy
The configuration has just two steps:
- Create Connectivity for the cloud and on-premises connections depending on your use case. As shown in the above figure. We have three cloud connectors for AWS, Azure, and Egress Internet traffic and one DX connector towards the on-premises data center
- Create a Traffic Policy to steer traffic toward the destination depending on your use case
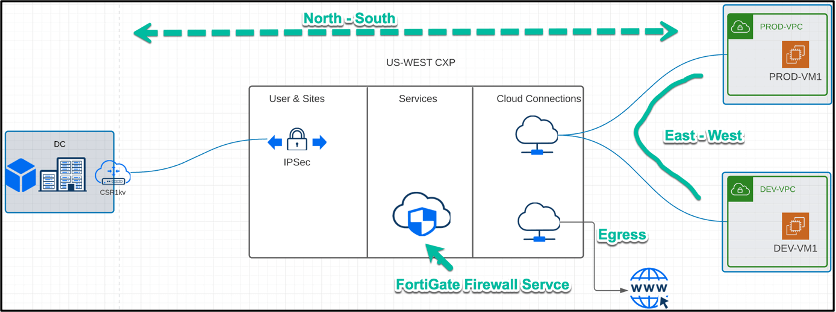
Figure 5: Traffic Flow for each Use Case
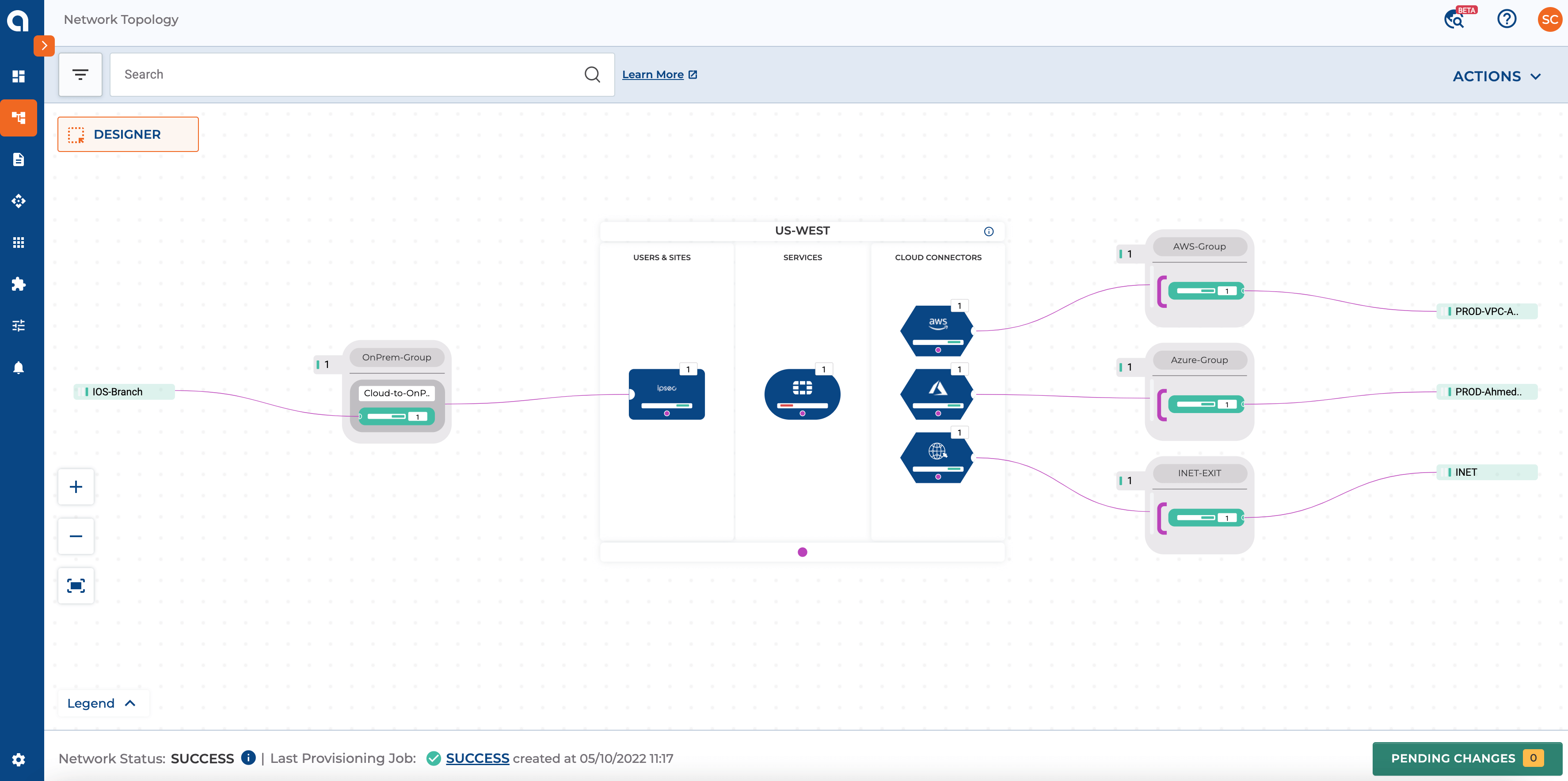
Figure 6: The above Screenshot highlights the Overall Network Connecting On-Premise and Cloud using Alkira CXP
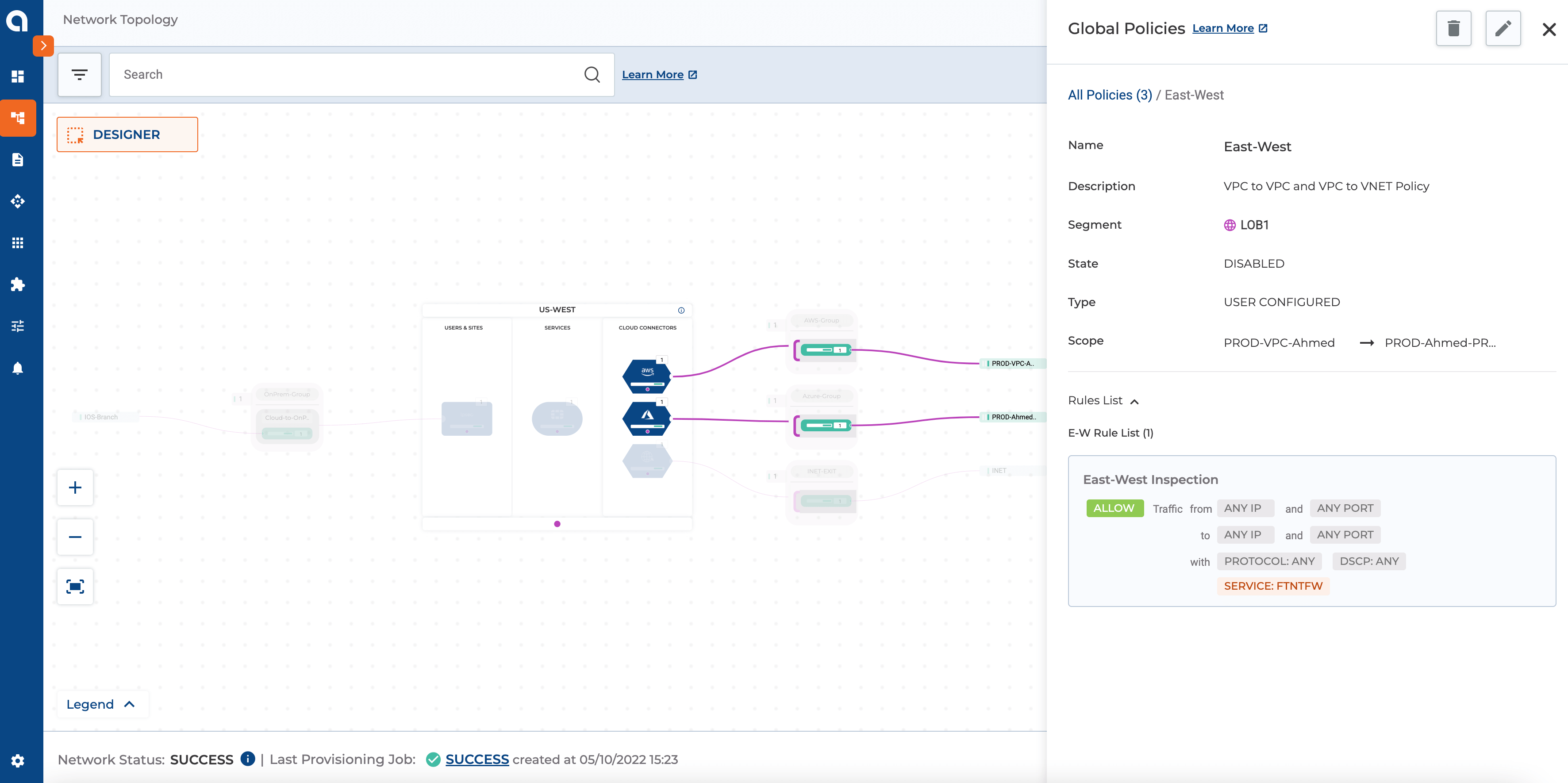
Figure 7: The above Screenshot highlights the policy for East-West Traffic Inspection
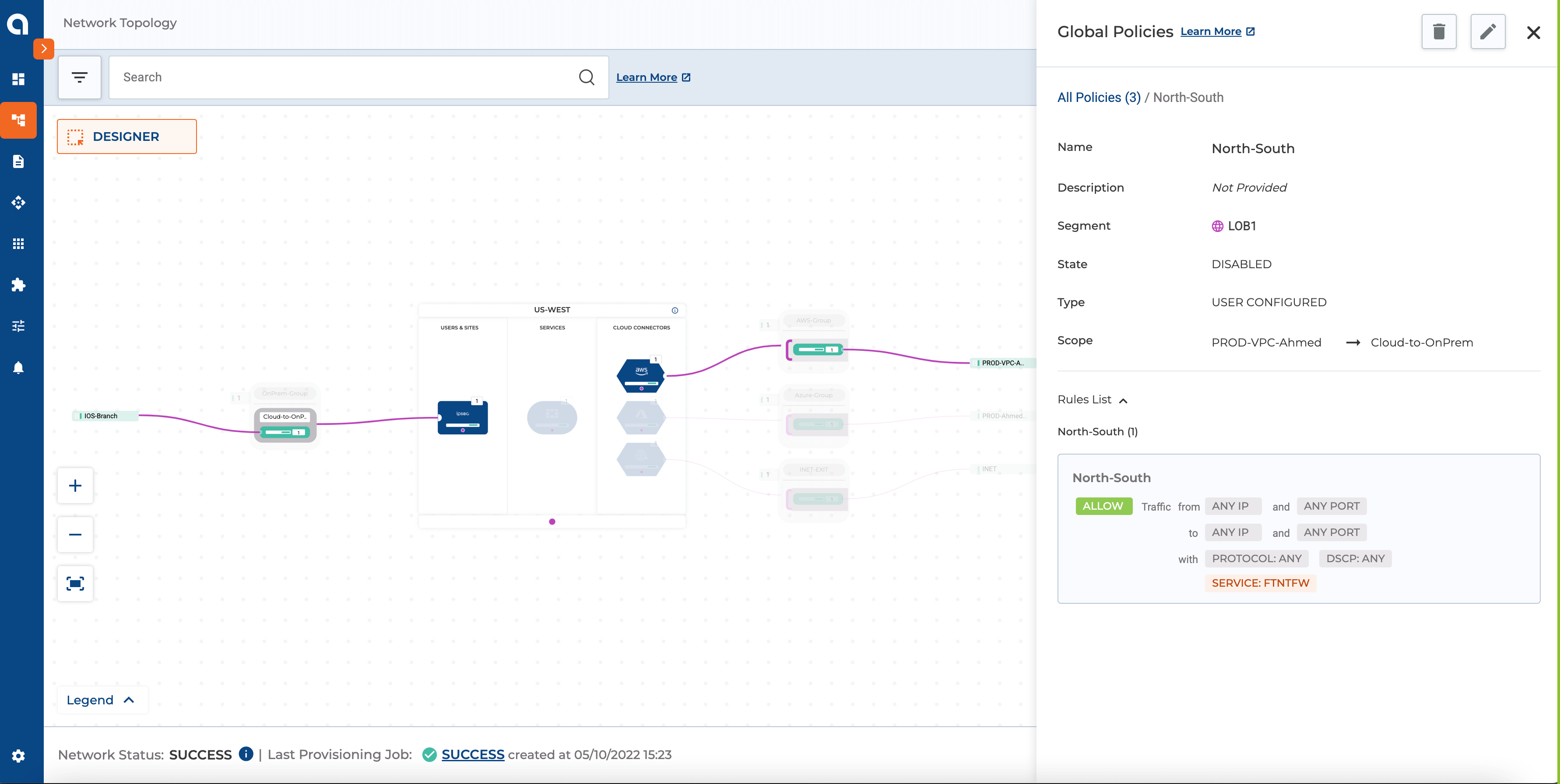
Figure 8: The above Screenshot highlights the policy for North-South Traffic Inspection
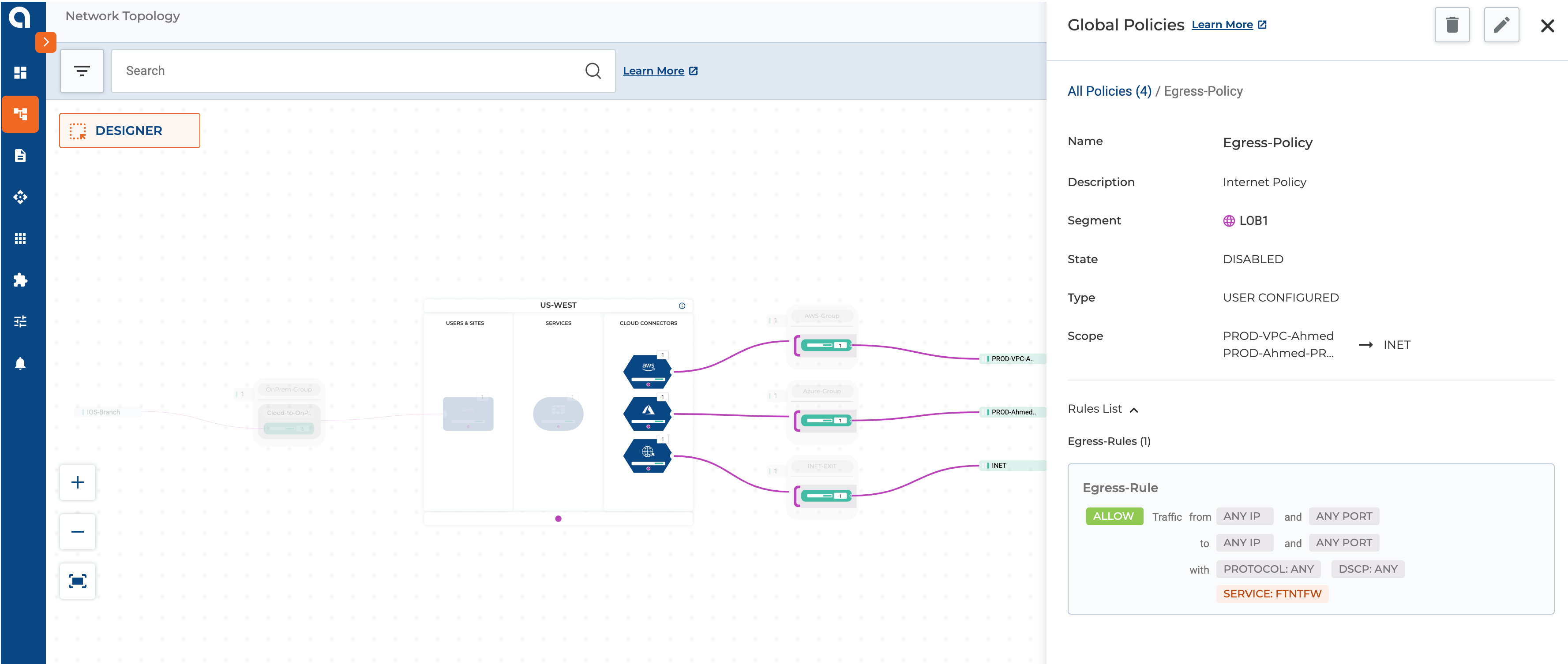
Figure 9: The above Screenshot highlights the policy for Egress Traffic Inspection
Alkira Solution Benefits:
Cost-Effective
In the Alkira solution, the same set of FWs can be used for multiple use cases, including inspecting east-west, north-south, and egress traffic which means that the user will not have to pay for various FWs based on region or the CSP that is being used.
Optimized & Efficient Design
The policy framework in the Alkira solution makes it easy to perform traffic redirection to the FW for any of the use cases mentioned above. This makes the design simpler since the user does not need to deploy multiple FWs for traffic inspection depending on multi-region or multi-cloud deployment.
FW resource Management
The Akira solution automates the FW lifecycle management and configuration of the FW infrastructure (interfaces, zones, etc.)
Troubleshooting
Troubleshooting tools such as Packet capture, flow capture, ping, and traceroute are part of the solution and help find the root cause of connectivity issues.
Modernize your cloud network with Alkira
To learn more about how Alkira can help simplify cloud networking for your organization, reach out and schedule a demo today.
You can also try our Cloud Insights tool for free here, giving you instant inventory and insights into your cloud networking resources.
Ahmed Abeer is a Sr. Product Manager at Alkira, where he is responsible for building a best-in-class Multi-Cloud Networking and Security Product. He has been in Product Management for more than ten years in different big and small organizations. He has worked with large enterprise and service provider customers to enable LTE/5G MPLS network infrastructure, automate Layer 3 Data Center, enable Next-Gen Multi-Cloud architecture, and define customers’ Multi-Cloud strategies. Ahmed’s technical expertise in Cloud Computing and Layer 2/Layer 3 network technologies. Ahmed is a public speaker at various conferences & forums and holds a Master’s Degree in Computer Engineering
Deepesh Kumar is a Solutions Architect and product specialist in the computer networking industry with over 8 years of experience. He currently works as part of the post sales team at Alkira and focuses on working with customers to design and deploy the Alkira solution. Prior to working here, he worked at Viptela which was acquired by Cisco Systems. He holds a masters degree from San Jose State University.





