Enterprises today grapple with a distributed workforce accessing resources from various locations and devices, blurring the lines between internal and external networks. This shift has created numerous security blind spots and expanded the attack surface, making it difficult to maintain consistent access controls and visibility across hybrid and multi-cloud environments.
Legacy VPN solutions, while familiar, often provide overly broad access and lack the granularity needed to enforce the principle of least privilege. Additionally, the increasing sophistication of cyber threats and the need for compliance with stringent data protection regulations further complicate the picture. That’s why we’re thrilled to announce Alkira Zero Trust Network Access (ZTNA) as part of our network infrastructure platform.
Starting with ZTNA Core Principles
Zero Trust Network Access has emerged as a crucial component of enterprise security strategies. At its core, ZTNA is built on three fundamental principles:
- Identity-based authentication and authorization
- Least privilege access to applications and resources
- Contextual security with near real-time adjustments to access

The value that these principles bring, lies in the ability to provide secure, granular access to applications and resources based on user identity and device posture, regardless of location.
Introducing Alkira ZTNA
Alkira ZTNA delivers comprehensive, scalable, and efficient zero trust access across all traffic flows—user-to-app, app-to-app, and user-to-internet—while maintaining network performance and simplifying management. ZTNA along with all other Alkira solutions can be controlled and managed via a single architecture, single portal, single user profile, and unified experience across the entire network.

Identity Driven
Who are you, and what are you allowed to do? Alkira’s approach to ZTNA starts with the end-user first by leveraging authentication and authorization via your preferred identity provider (IdP), which restricts access to required resources and applications ONLY.
Context Aware
Once you have access to applications and resources on the network doesn’t mean you should ALWAYS have that access. Alkira introduces advanced posture assessment which provides crucial information about the connecting device, allowing for more nuanced, context-aware decisions about granting or restricting access.
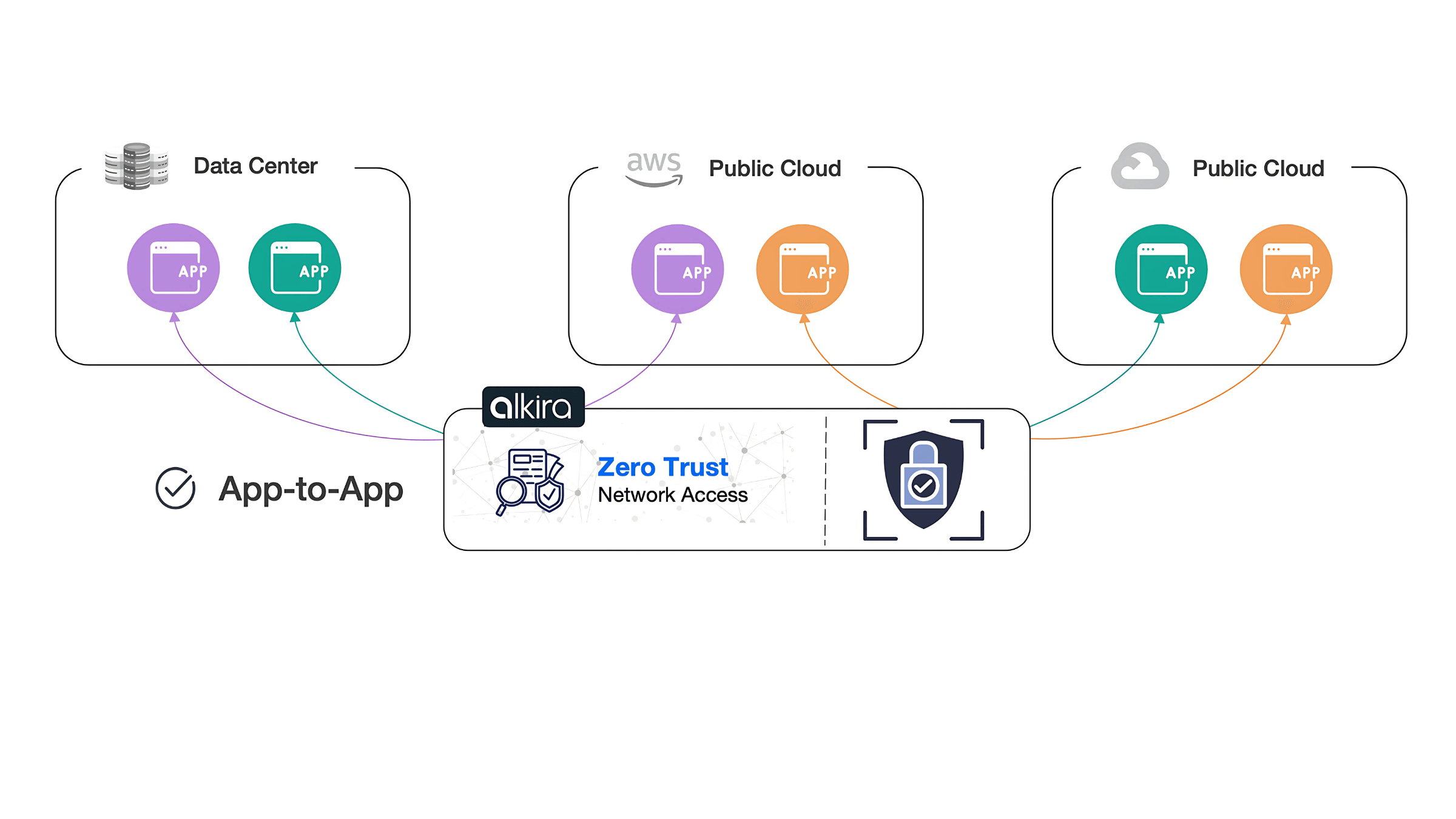
Zero Trust for App-to-App Connectivity
Today, enterprises must contend with securing applications that live in their own data centers, across multiple public cloud providers, and as-a-Service offerings. Many times, these applications need to communicate securely with one another without sacrificing performance. With Alkira ZTNA, App-to-App security can be enforced and managed just like all other solutions in the platform, all through the same portal.
The Alkira Advantage
By choosing Alkira ZTNA, you’re not just getting another bolt-on solution—you’re gaining a complete platform for your journey towards a more secure, efficient, and flexible network infrastructure. Ready to enhance your network security? Contact us today to learn more about how Alkira ZTNA can transform your approach to secure access.